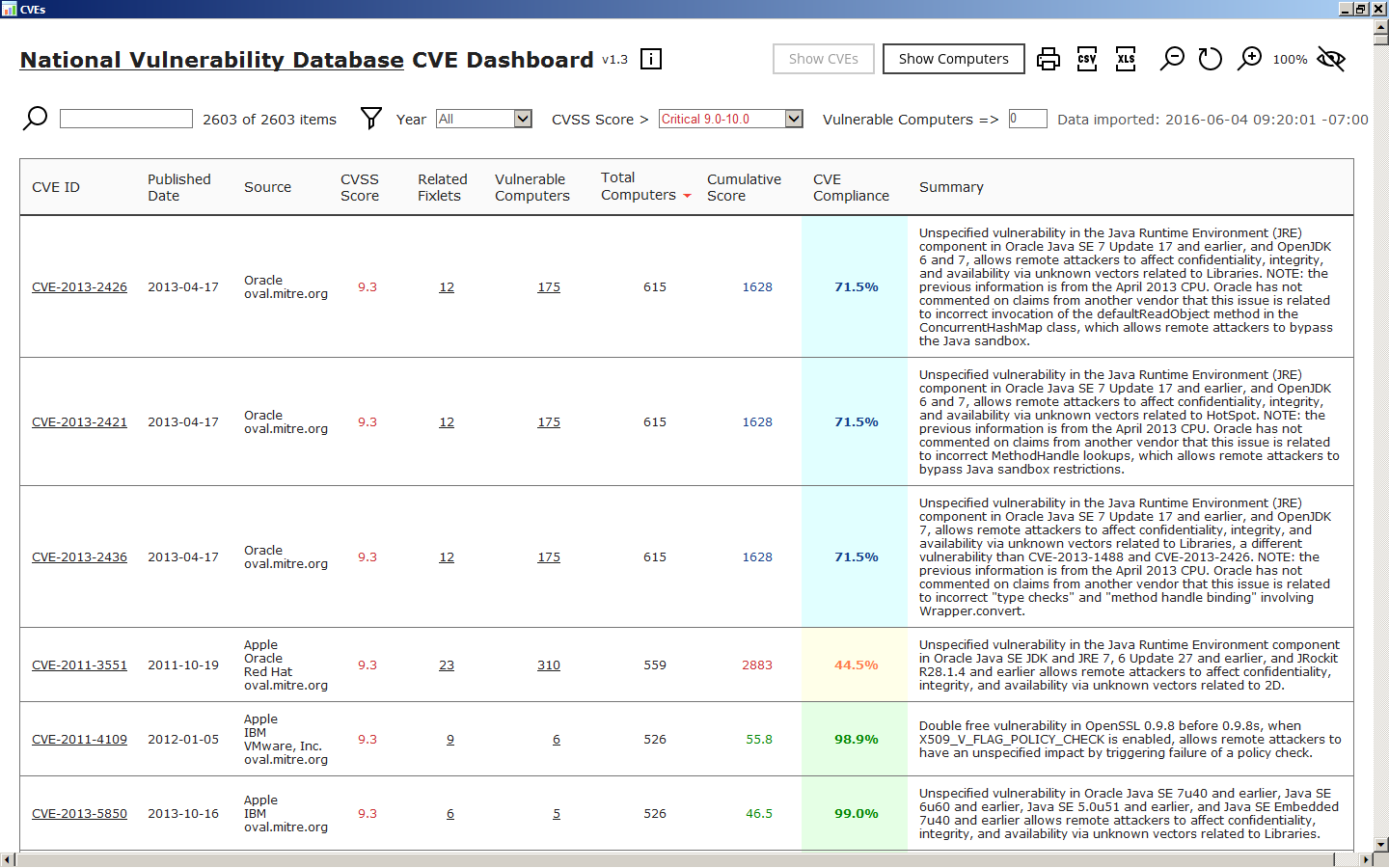
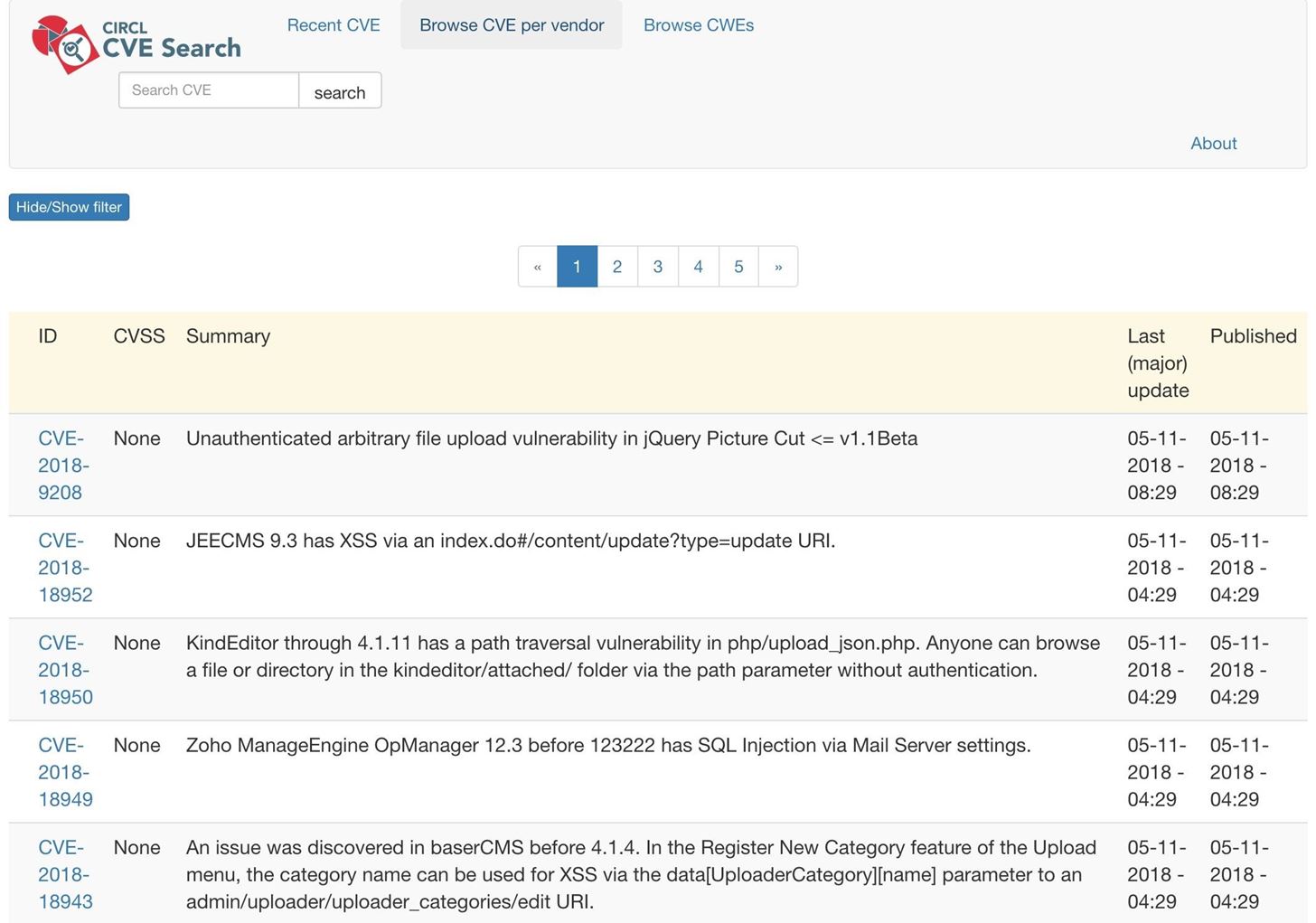
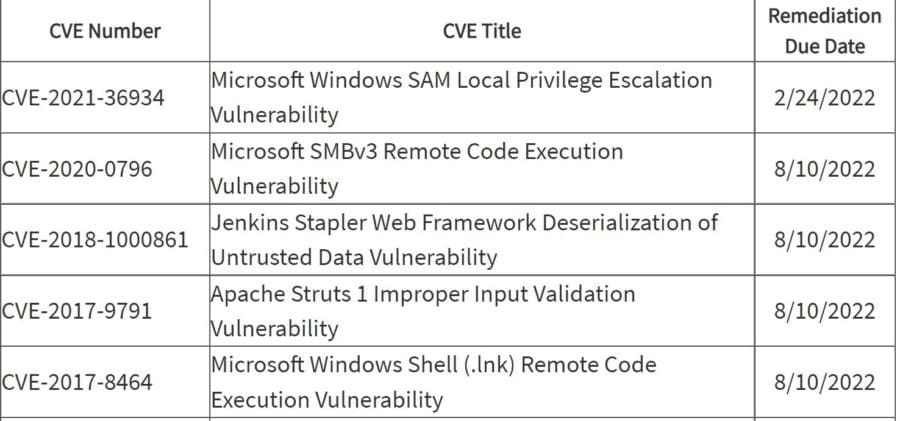
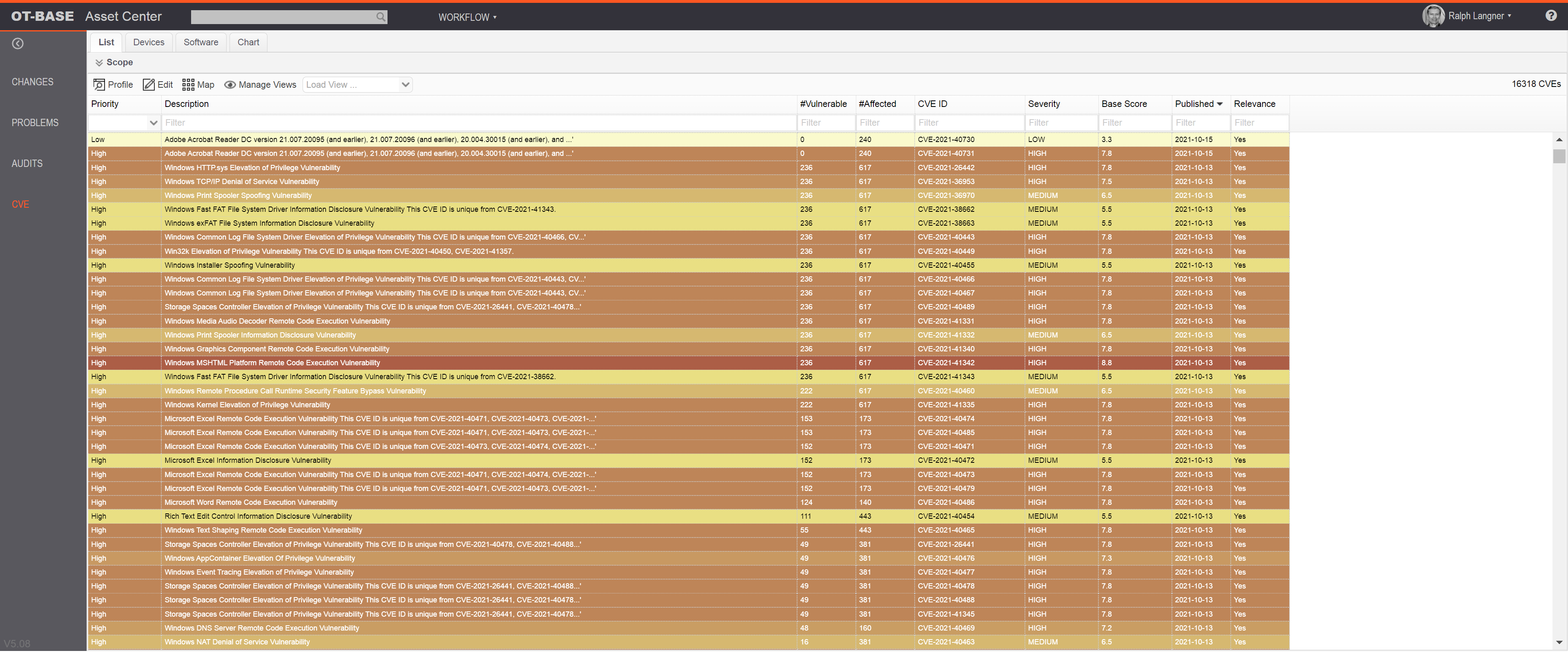
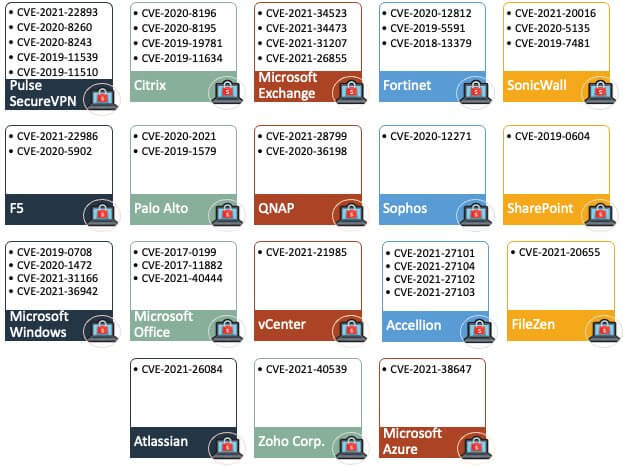
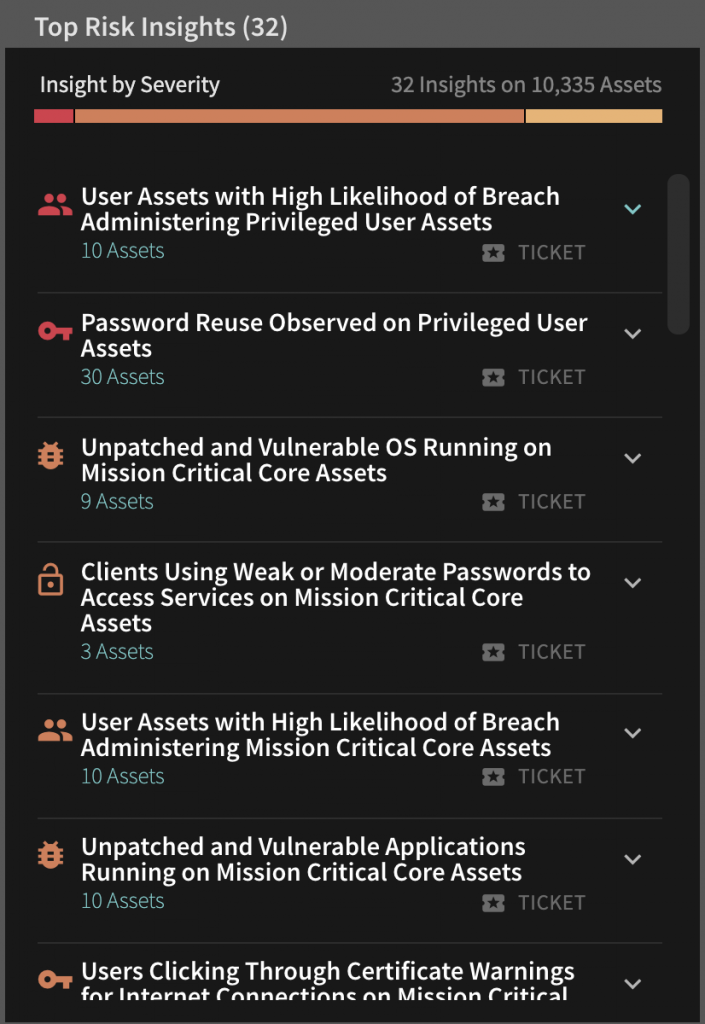
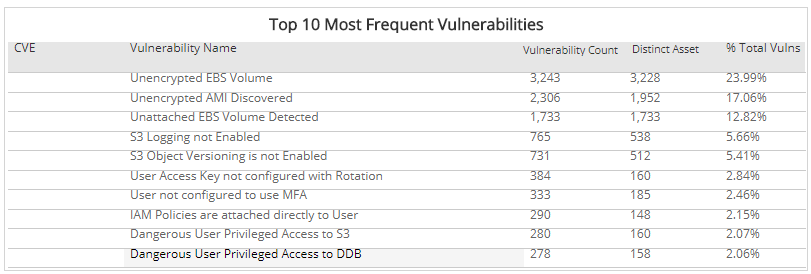
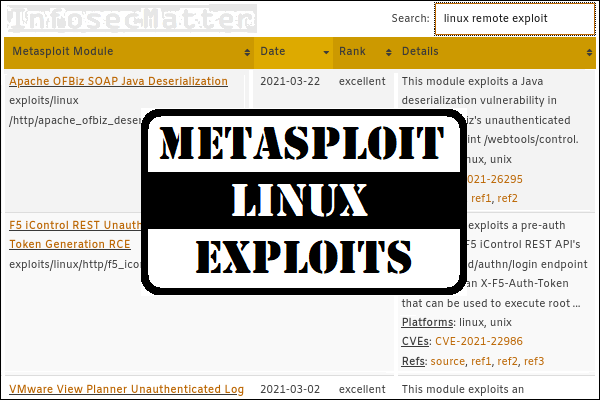
ExploitWareLabs - CVE List for AttackDetection(snort rule) Cc @AttackDetection https://github.com/ptresearch/AttackDetection | Facebook

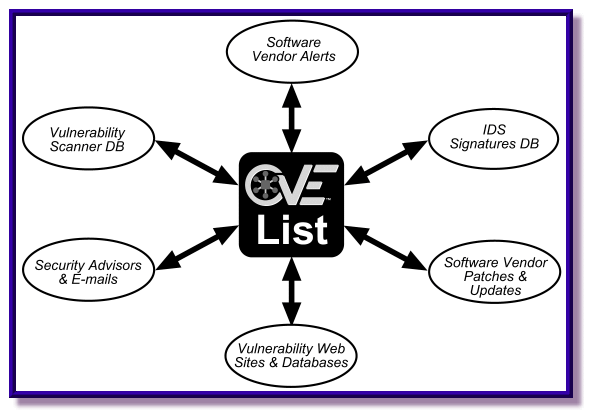
IPA Information-technology Promotion Agency, Japan : IPA/ISEC:Vulnerabilities:CVE (Common Vulnerabilities and Exposures) Overview